Man-In-The-Middle attack on an Android Virtual Device with Burp Suite
Struggling to sniff Android app traffic with Burp Suite? I was too—until I rooted my AVD, wrangled trust stores, and got full MITM working. Here's the full step-by-step guide, minus the tears.

Hi again, my dearest readers!
This is a follow-up in our new Android Security Series on The Hacking Diaries.
For us pentesters and bug bounty hunters, sniffing an application's network traffic is essential. But with recent changes in Android’s architecture and security patches, doing this has gotten trickier—and, honestly, a bit confusing. (At least for me. hehehe.)
After plenty of research and trial-and-error, I finally managed to pull off a successful Man-In-The-Middle (MITM) attack to sniff both APK and browser traffic. Here's how.
Why is this so confusing?
Because of Certificate Trust Stores!
Let’s break it down. A trust store is a repository in your device that contains certificates used to authenticate secure connections. These certificates hold identity information about entities (such as a server), verified by a Certificate Authority (CA). They enable encrypted communication through SSL/TLS protocols.
These days, Android devices come with two trust stores:
- User Certificate Trust Store → You can manually add a CA here via your phone’s settings. Straightforward.
- System Certificate Trust Store → These CAs come pre-installed with the OS and can’t be changed—unless the device is rooted.
We’ll be adding a CA to the system trust store for testing purposes. You’re not supposed to... but we are.
Why go through all this trouble to add a CA to the System Trust Store?
Because most apps don’t trust user-installed CAs by default—unless it’s explicitly stated in their network security config.
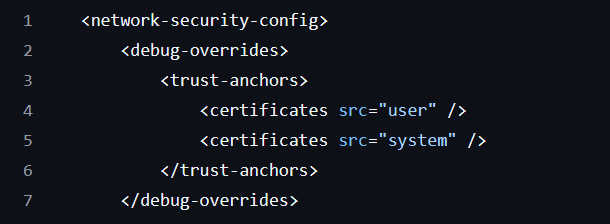
But even if the app does trust User CAs, you may still hit snags. For example, WebViews don’t trust the user store, even if the app does. So you'll end up missing its traffic.
Installing your proxy's CA in the System Trust Store solves this problem once and for all.
Enough introduction for now, let's check the steps you need to get yourself those lovely HTTP requests.
Hacking your device.
The fun part!
You’ll need a rooted Android Virtual Device (AVD). We’ve already covered that, so once yours is ready, here’s what to do:
- We'll first install the Magisk module needed for moving our User installed CAs to the System CAs.
- Go to https://github.com/NVISOsecurity/MagiskTrustUserCerts/releases and download the latest release of the tool. Then push it to you AVD by running
adb push AlwaysTrustUserCerts.zip /sdcard/Download- Now inside your Android device, open the Magisk app and go to the Modules tab. Then click on "Install from storage" and search through your files till you find the .zip you just uploaded.

- Double-click to installed it, then confirm installation and reboot your device.
- Cry while your device is rebooting. (Let that frustration out of your body!)
Configuring Burp Suite's Proxy and Certificate Authority.
We are almost there!
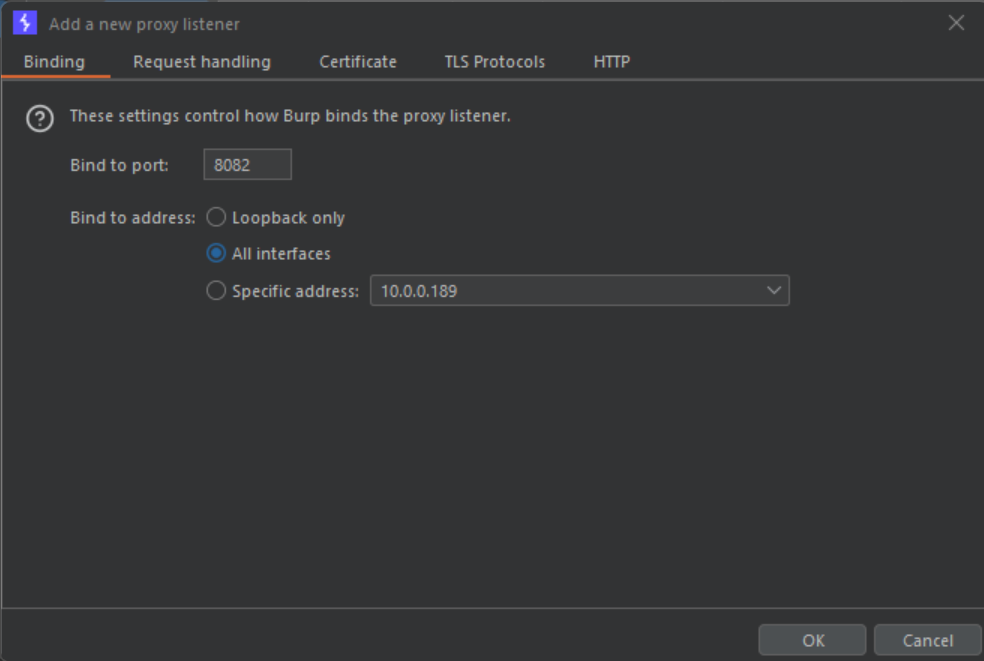
- Go to your Burp Suite program, then click on the "Proxy" tab, and once there, go to "Proxy Settings" where a new window will pop up.
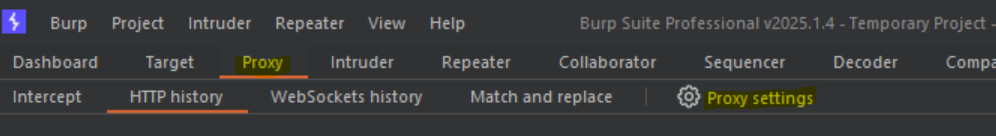
- Create a new Proxy Listener. For that, click on "Add", bind any free port you have and select "All interfaces". That's it, go ahead and click OK. You don't need to touch anything else.
- Now, as we have been talking a lot about certificates and certificate authorities, it's time for us to get our CA and install it into our Android device. (AVD in my case, but could be physical as well, provided that it is rooted.)
On the "Proxy Settings" page, we need to click on "Import / Export CA certificate" and then select to export the certificate in DER format.
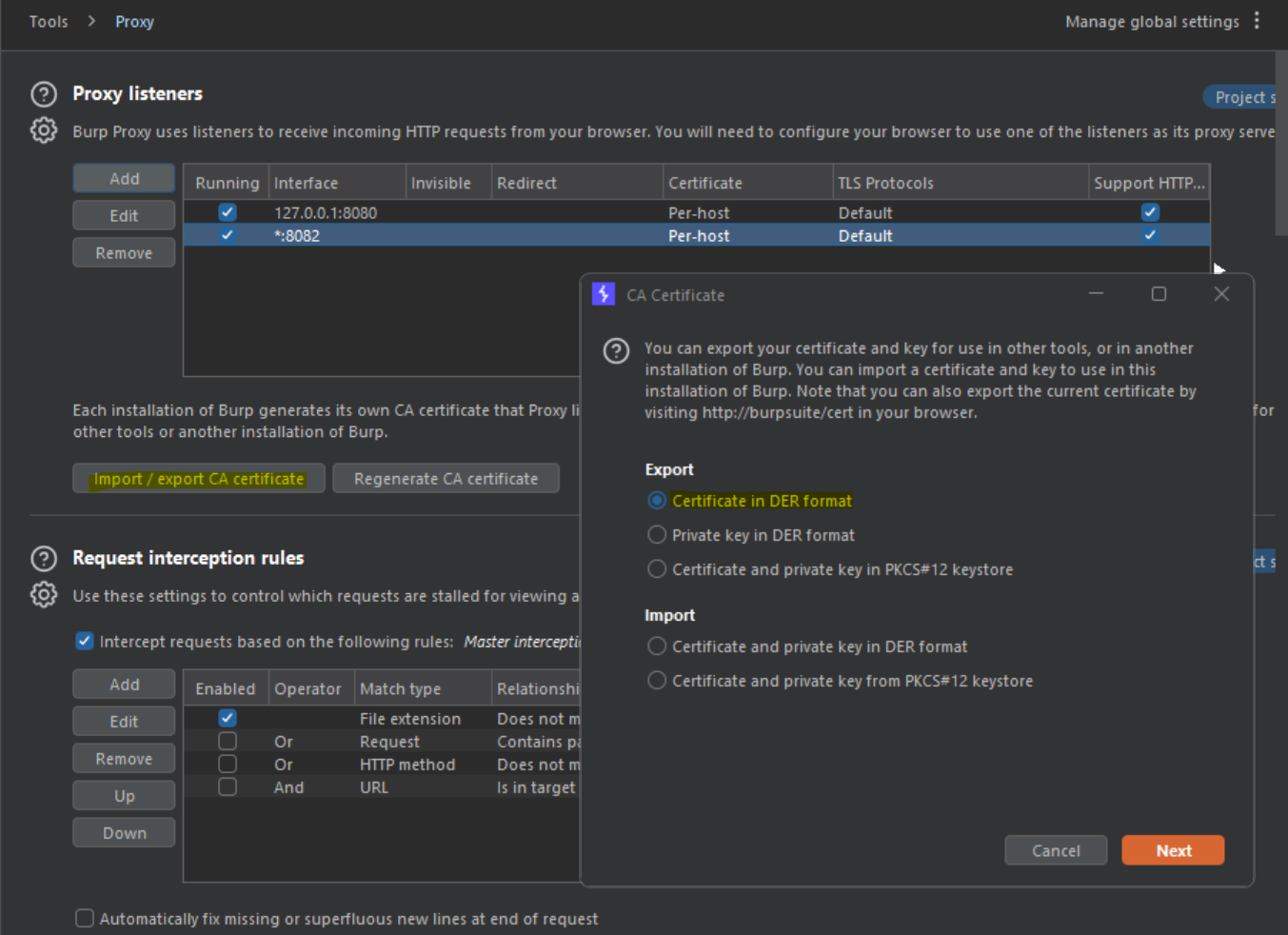
- Click "Next", and when selecting where to export the certificate, change it's extension to .crt . Any name works, but your Android device needs it be a .crt file type.
- With your certificate at hand, just drop it inside your AVD or push it through the command line like:
adb push certificate.crt /sdcard/Download- Now head to your Android Settings > Security > Advanced > Encryption and Credentials > Install a certificate > CA certificate. It will show a warning because of the security concerns implied, but we all know why we are doing this and you should have permissions to do so, therefore click on "Install anyway". Navigate through the device's files until you find the .crt we just uploaded.
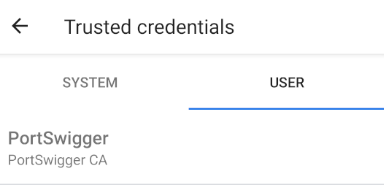
- Once it is installed, you can see it on the Trusted Credentials option > User tab. But it won't be on the System's CAs tab. (for now)
- Reboot your device using adb:
adb rebootThe AlwaysTrustUserCerts module we previously installed will move your certificate to the system's CAs on reboot.
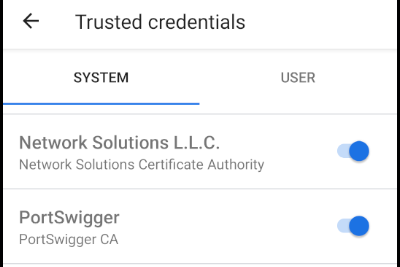
- Wait for your device to boot and check that your CA is now in your System Trust Store. Luckily, you'll have done it correctly!
Configuring the device to use your Proxy.
The final step!
Now that we were able to:
- Root the device.
- Install a module that moves our CA to the System Trust Store.
- Configure Burp Proxy Listener.
We need to configure the Proxy in our device in order to start intercepting data. So, the final steps are:
- On your device, go to your WIFI settings, select the network you are connected to, and edit it like you see below. Then hit "Save".
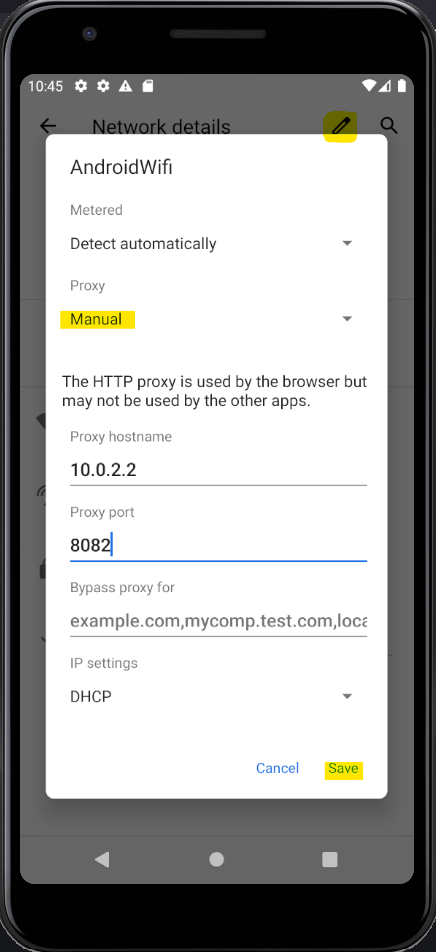
- Open the device's Browser. And check your "HTTP History" tab on your "Proxy" section inside Burp's application. Do you see any traffic?
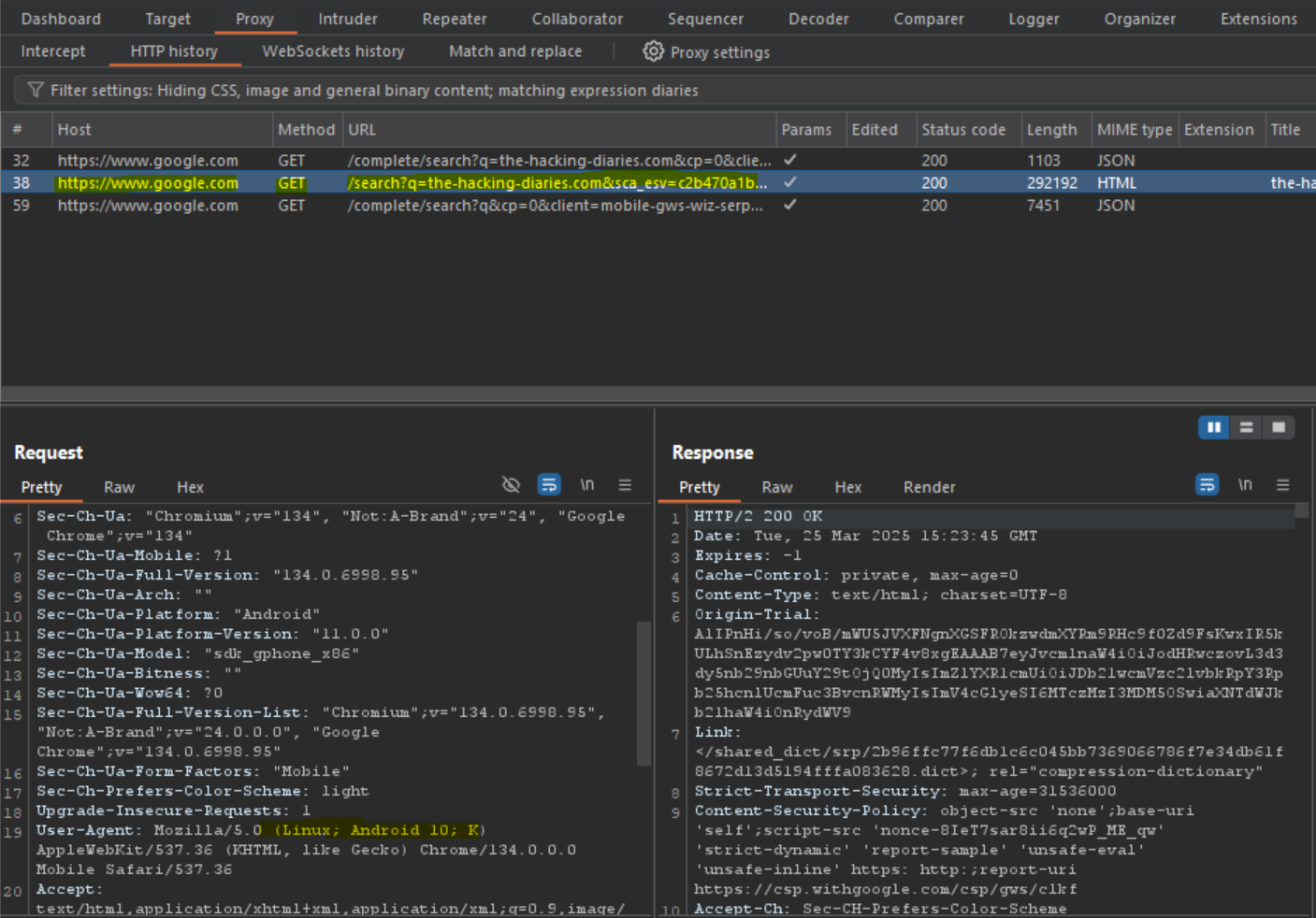
If yes, well done! You were able to intercept the browser's traffic. Now it’s time to check the application's network activity.
- Clear your history on Burp to start with a clean slate and open your target mobile application, use it and mess around, maybe log in as well. Go back to Burp and check if you have requests coming from the mobile device.
- Succeeded? Go ahead and drink something tasty on my behalf. Didn't work? Go back and redo the needed steps.You’ll get there. We’ll celebrate later.
That’s it! Thanks for sticking with me through this one.
Honestly, I struggled with this way more than I care to admit. It took days of research, but now that it's all written down... it seems kinda simple.
BUT IT WAS NOT.
Happy Crying—I mean... Hacking!




